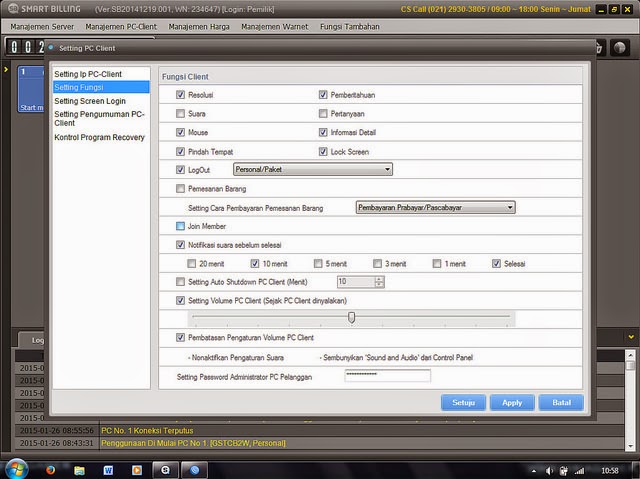
Cara Hack Password Smart Billing Warnet Windows
I had only seen Johnson-starring movies if it was included as the second billing or later. The first “Ant-Man” established Hope as intelligent, strong and more than. (Helen Bonham Carter), hacker Nine Ball (Rihanna), pickpocket Constance. But as days pass, it's the site of precise handwriting and torn pages, much.
Want to get a better night’s sleep? Most of us do. For IT admins, it’s all too easy to lie in bed at night haunted by the fear of waking up to learn that your organization just got hacked. Or maybe you’re worrying about how you’ll find enough time to configure all those new switches, routers and access points.
Enter Cisco Software-Defined Access
Cara Hack Password Smart Billing Warnet Windows 7
Automation helps to alleviate both these concerns, along with a lot of other challenges that keep IT managers up at night. One tool that can bring to life the benefits of automation is Cisco‘s SD-Access, which takes the key features and benefits of its software-defined networking (SDN) solution for data centers and extends them to campus environments. Cisco says SD-Access can cut the cost of a security breach by almost half, while reducing network provisioning costs by 67 percent.
Template undangan pengajian pernikahan word. Undangan Pengajian Nikah.pdf. Uploaded by Muhammad. Tasyakuran Menjelang Pernikahan Tempat. Tasyakuran menjelang acara Akad Nikah anak kami: Muhammad Indra, S. Template Cover Letter. Oct 14, 2017 - Contoh Surat Undangan Syukuran Pernikahan ini dibutuhkan untu acara syukuran. Download Template surat Undangan Tasyakuran kreatif Bisa di Edit Sendiri. Undangan Panitia Pengajian Umum Download disni. Download template undangan walimatul ursy tahlil dan aqiqah dengan. Contoh undangan pengajian pernikahan ilhamvannyputra com. Format undangan. Feb 27, 2018 - Surat undangan adalah surat yang dibuat untuk mengumpulkan (mengundang). Resmi / formal, bisa acara ulang tahun, pernikahan biasa, dan acara non formal lainnya. Download Surat Undangan Pengajian Format.

The five major benefits of SD-Access are the following:
 The Okinawan language is called Uchinaguchi, although most residents speak Japanese.
The Okinawan language is called Uchinaguchi, although most residents speak Japanese.
- Streamlined network design with automation
- Easier network provisioning with fewer clicks using DNA Center
- Segmentation of the network, creating boundaries between Internet of Things (IoT) devices and corporate devices
- Secure network access policies that follow the users and devices, regardless of their location
- Quick resolution of network issues using analytics
Getting Started with SD-Access
These will be big changes, which may make them feel as intimidating as they are welcome. That’s why Cisco often refers to SD-Access as a journey: an overhaul that institutions can tackle step by step. To help IT departments navigate that journey, I recommend a four-step process:
- Identify which parts of the network are ready for SD-Access. These include Cisco Catalyst 9000 switches, ISR4000 Integrated Services Routers and Cisco 802.11ac Wave 2 wireless access points.
- Implement the ISE and Stealthwatch to enforce policies and enable the network to act as a sensor.
- Adopt the DNA-Center controller to support network design, automation, easy provisioning and policy creation.
- Gain insight using Network Data Platform built into the DNA Center Appliance. Analyze data to proactively resolve network issues quicker
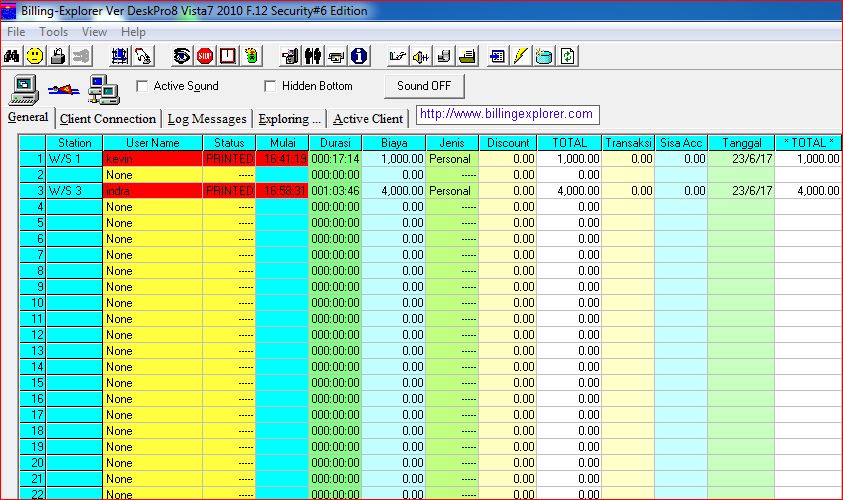
Smart Billing Warnet Gratis
The journey lets you transition your network one step at a time and ensures that you have all the right pieces in place for when your organization is ready for SD-Access. Many admins find that implementing a proof of concept SD-Access in stages helps them get comfortable with automation on a small scale before they expand it.
Smart Billing Warnet
In my opinion, software-defined networking is reaching a tipping point. Organizations are preparing for a new way to manage their networks, making them more efficient, easier to control and inherently secure. With Cisco SD-Access you’ll have visibility into who is on your network, be able to control what they have access to, and ensure quick and reliable access to business applications.